Sorting Through Sovereign Network Infrastructure

Across Canada’s public sector and regulated spaces, sovereign network infrastructure is a mainstream concern: how do we stand up centrally managed switching that talks cleanly to a SIEM, keeps operational data in Canada, and does not blow up the budget?
For IT and security leaders, understanding the complexity here is essential to build infrastructure that works. Public institutions, universities, healthcare providers, and municipalities are all under FIPPA (or equivalent provincial acts) and must balance operational resilience, security, and compliance, and always on constantly shrinking budgets.
Sorting through this landscape isn’t simple. The market is crowded with vendors who promise “enterprise compliance” on one side, and low-cost disruptors on the other. The challenge is determining what is truly necessary for a secure, truly sovereign environment, and what is little more than compliance theater.
Let’s set a pragmatic baseline, look at the options that are actually available here, walk through costs that matter in real life, and separate sovereignty from paperwork. Then compare the “enterprise compliant” stacks with solid, lower-cost alternatives. I will also include a quick comparative listing of switch models with Canadian pricing so you have a feel for hardware dollars.
What “good” looks like
Layer 2+ managed switches Think full Layer 2 plus a few Layer 3-lite features. In practice you want VLANs, 802.1X, ACLs, QoS, IGMP snooping, LACP, and static routes. That is the minimum for clean segmentation and basic hygiene across campus or branch.
SIEM-integrable telemetry Your switches and controllers should export syslog with predictable fields, stay on time with NTP, and use TLS where supported. You should be able to send logs straight to a sovereign SIEM like Wazuh, Elastic Security, Splunk, or IBM QRadar without passing through a non-Canadian cloud (eliminates Microsoft Sentinel).
Central management without non-sovereign dependency Controllers need to run on-prem or in a Canadian tenant you control. Cloud-optional is fine. Cloud-required is not. The difference in Canada vs the US is that Canadian companies are vulnerable to FISA and the Cloud Act without having any rights or any restrictions in place. In the US, organizations are protected by due process and constitutional rights. In Canada there are no bi-lateral agreements which equals zero protections.
The Switch Management Landscape in Canada
At the high end, you’ll find the “enterprise compliance stacks”: Cisco DNA Center, HPE/Aruba Central, and Juniper Apstra. These platforms bring PSIRT bulletins, SOC 2 attestation, and FIPS 140-2 validated cryptography — the kind of certifications auditors and compliance officers like to see. They also carry six-figure price tags for large rollouts.
Aruba (HPE) is relatively affordable in this tier. Aruba Central On-Prem (COP) provides full sovereignty, can run on your servers, integrates with PAM/IAM, and produces the vendor-signed compliance artifacts (SOC 2, ISO 27001, FIPS 140-2). For Canadian institutions, Aruba COP is often seen as the “least-expensive enterprise-compliant” option.
Cambium sits in the space between enterprise and SMB. With cnMatrix hardware and cnMaestro On-Prem, they offer a free Essentials tier and a paid X tier, combining enterprise-class telemetry with more flexible pricing. Below that enterprise line are the clear SMB-oriented stacks: TP-Link Omada, D-Link Nuclias Connect, Ubiquiti UniFi/UISP, and FS.com FSOS with AmpCon. All of these deliver Layer 2+/Layer 3-lite switching, syslog export, and self-hosted controller options, and all have improved their posture in recent years. TP-Link has added ISO 27001/27701 corporate certifications and formalized its vulnerability disclosure process. D-Link has kept Nuclias Connect as free on-prem software with structured firmware advisories and a push toward ISO/IEC 27001 alignment. Ubiquiti, while not pursuing SOC2 or FIPS validation, has increased cadence and transparency in patching and offers ongoing CVE publication. FS.com holds ISO 9001/14001/45001 certifications and now produces clearer release notes and advisories tied to its PicOS/AmpCon ecosystem. Cambium, in parallel, has layered on more formal patch cycles, structured support pathways, and SIEM-friendly telemetry. The net result is that the SMB and mid-market vendors are no longer “hobbyist” players as they have all built a more credible compliance and certification story over the last five years, even if they do not package the same audit artifacts that Aruba or Cisco provide.
- HPE Aruba (Aruba Central On-Prem or AirWave) On-prem controller option with device-type licensing. Aruba CX is common in EDU, health, and municipal. If you MUST show vendor attestations and want a strong TAC story, this is usually the least expensive of the true enterprise stacks.
- Cambium (cnMaestro On-Prem + cnMatrix) cnMaestro Essentials delivers full centralized telemetry and management, making it well-suited for sovereign deployments and the majority of enterprise needs. cnMaestro X (paid subscription) layers on enterprise-grade capabilities such as AI-driven analytics, extended data retention, API integrations, advanced onboarding controls, MSP workflows, enhanced TAC, and deeper switch diagnostics.
- Ubiquiti (UniFi and UISP) Self-hosting UniFi Network and UISP is free. UISP’s hosted plan is now paid, so for sovereignty you self-host. Very popular in SMB, K-12, and lab spaces.
- TP-Link Omada (software controller on-prem) The on-prem Software Controller is free. Licenses only apply to the Omada cloud controller, which we are not using here. JetStream switch pricing in Canada is extremely aggressive.
- D-Link Nuclias Connect Free on-prem controller that manages D-Link smart and managed lines. Their DGS-1210 series is a low-TCO workhorse for a lot of branch and access roles.
- FS.com (FSOS switches with FS NMS or AmpCon-Campus) L2+ switching with on-prem management. Controller licensing is per device. C$176 for 1 year, C$244 for 3 years, C$299 for 5 years per device.
On-prem add-ons you can pair with any of the above
- SolarWinds Network Configuration Manager Self-hosted config backup, golden config, drift checks, and policy reporting. Licensed by node count.
- PacketFence Open-source NAC. Full 802.1X and RADIUS, captive portal, VLAN enforcement. Free to run, you budget servers and time or buy support.
The Compliance Industry vs. Real Security
This is where the gap between security and compliance is clearest.
Take FIPS 140-2. It’s a U.S. standard for cryptographic module validation. Aruba and Cisco trumpet FIPS certification, and auditors love it. But in practice, if your switch encrypts management traffic with AES-256, forwards logs securely, and you’ve documented your controls, your environment is just as secure, whether or not the vendor has paid to validate through NIST’s Cryptographic Module Validation Program (CMVP).
Researchers have long critiqued FIPS validation as more bureaucratic assurance than technical superiority (see: NIST CMVP program notes, critique in IEEE Security & Privacy). Yet compliance frameworks continue to elevate it as a “must have.”
The reality: a large part of the cost delta between Aruba COP and the mid market vendors is not technical security — it’s the paperwork.
Sovereignty versus “paper sovereignty”
A vendor can be “compliant” on paper and still default to foreign services. Real sovereignty is an engineering choice. Self-host the controllers, terminate TLS locally, and keep logs, configs, and identities inside Canada. Compliance frameworks help, but they do not replace architecture. FIPS 140-2 is a good example. It validates crypto modules and may be written into a contract, but it is not proof your overall design is secure. Treat it as one control, not a proxy for everything else.
Who actually demands formal compliance? In practice this comes from your organization or a contracting client. It is usually a governance or contract requirement, not automatically the law. If they want specific attestations or modules, you plan and cost for that.
Side-by-side switch costs in Canada
These are representative, in-stock public listings captured 6 Sep 2025. Prices move quickly, so treat them as directional and validate with your reseller.
HPE Aruba CX
- CX 6100 48G PoE 370W (JL675A): about C$4,160 list
- CX 6100 24G PoE 195W (JL677A): about C$2,731 list
FS.com S-series
- S3410-48TS 48×1G L2+ non-PoE: about C$1,724 PoE variants are quote-only, so expect higher
TP-Link Omada JetStream
- TL-SG3428MP 24-port PoE+ 384W: about C$459 at volume, usually under C$600 single-unit
- TL-SG3452P 48-port PoE+ 384W: roughly C$611 to C$715 Non-PoE TL-SG3452 often around C$460
D-Link Nuclias Connect, DGS-1210 series
- DGS-1210-28P 24-port PoE: about C$500
- DGS-1210-28MP 24-port PoE 370W: about C$610
- DGS-1210-52MP 48-port PoE 370W: about C$870 to C$920
Ubiquiti UniFi
- USW-48-PoE 48-port PoE 195W: about C$799
- USW-24-PoE 24-port PoE 95W: about C$429
Cambium cnMatrix
- EX2052-P 48-port PoE 370W: about C$2,015
Rule of thumb: Aruba and Cambium are more expensive but bring deeper enterprise ecosystems and TAC. TP-Link, D-Link, Ubiquiti, and FS often land at 25 to 60 percent of Aruba’s price for similar port counts. The trade-offs are platform maturity, documentation depth, and the amount of “paper” you have to produce yourself.
Controller and license costs that keep you sovereign
- Aruba Central On-Prem Device-type subscriptions in 1, 3, 5, 7, and 10 year terms. Budget roughly C$250 to C$450 per switch per year until you have a quote.
- Cambium cnMaestro On-Prem Essentials is free. cnMaestro X is paid per device.
- Ubiquiti UniFi and UISP Self-host is free. Hosted is paid. For sovereignty you self-host.
- TP-Link Omada On-prem Software Controller is free. The cloud controller is the thing that is licensed.
- D-Link Nuclias Connect Free on-prem software. There is also an optional hardware hub if you want an appliance.
- FS.com Per-device controller licensing: C$176 for 1 year, C$244 for 3 years, C$299 for 5 years.
- SolarWinds NCM Node-based. Plan on roughly C$3K to C$11K depending on tier and node count.
- PacketFence No license. Budget engineering time or commercial support.
What the money really buys
If your org or your client wants vendor attestations and a strong TAC story, Aruba or Cambium reduce audit friction. If the real requirement is sovereign operation without specific paperwork, on-prem TP-Link, D-Link, Ubiquiti, and FS meet the technical bar with solid design and documentation.
The hidden cost is rarely firmware. It is the evidence you have to show: your access model, SSO or PAM configuration records, log retention, baseline configs, and a patch register that proves you met your SLA. Big platforms ship templates and “policy” reports, but you still have to integrate them into your SIEM and evidence library.
What the enterprise vendors really save you is the time spent assembling third-party attestations (SOC 2 reports, FIPS certificates, ISO mappings) and the credibility of a vendor-signed PSIRT program.
all IT departments that are required to supply compliance reports must:
- Prove SIEM forwarding (screenshots, log samples, retention settings).
- Document SSO/PAM integration and RBAC roles.
- Maintain a patch register (advisory date, applied date, scope).
- Show lifecycle management (EoL timelines, replacements).
The difference is whether you also have to build a control-to-framework mapping yourself or can drop vendor docs into the audit pack.
When Compliance Reports Are Actually Necessary
Compliance evidence is only mandatory when:
Your organization has adopted a compliance framework (e.g., SOC 2, ISO 27001, FIPPA-driven ITGCs)
Your contracting client explicitly demands attestations in the RFP or contract.
Your regulator mandates it (e.g., healthcare in some provinces, financial services).
For universities, municipalities, and smaller healthcare orgs, FIPPA requires privacy protection but does not dictate vendor attestations. In those cases, sovereignty and engineering practices (patching, SIEM logging, RBAC) matter more than whether a switch is FIPS-validated.
Compliance & Cost by Vendor
Aruba (HPE)
- Licensing: Highest cost (~C$250–450 per switch per year).
- Compliance artifacts: Strongest in class — SOC 2, ISO 27001/27701, FIPS 140-2, formal PSIRT advisories, lifecycle bulletins, vendor-signed audit documentation.
- Labour: Still required — SIEM forwarding proof, RBAC/SSO documentation, patch registers, lifecycle planning. Vendor attestations reduce mapping work.
- ~25–30 hours over 5 years (~C$3–4K).
- Takeaway: Expensive, but lowers audit prep effort where SOC/FIPS/ISO paperwork is mandatory.
Cambium (cnMaestro + cnMatrix)
- Licensing: cnMaestro Essentials is free; cnMaestro X is a paid add-on.
- Compliance artifacts:
- Essentials: advisories and telemetry, but short retention and fewer reports.
- X: adds longer historical data, APIs, MSP workflows, better audit support.
- Labour:
- X: ~30–35 hours (~C$4–5K).
- Essentials: ~40–45 hours (~C$5–6K).
- Takeaway: Essentials is fine for sovereignty; X narrows the gap with Aruba if you need reporting longevity and formal support.
FS.com (FSOS + AmpCon-Campus)
- Licensing: Per-device controller license — C$176 (1 yr), C$244 (3 yrs), C$299 (5 yrs).
- Compliance artifacts: ISO 9001/14001/45001, release notes and advisories. No SOC 2, no FIPS. No vendor-signed audit pack.
- Labour: Operator must prepare full compliance pack: patch registers, RBAC/SSO docs, SIEM proof.
- ~40–45 hours (~C$5–6K).
- Takeaway: Much cheaper licensing than Aruba, but higher compliance work internally.
TP-Link (Omada)
- Licensing: Free on-prem Software Controller; cloud-only is licensed.
- Compliance artifacts: ISO 27001/27701 corporate certifications, vuln disclosure portal. No SOC 2/FIPS.
- Labour: Similar to FS.com — patch registers, SIEM proof, RBAC docs all operator-built.
- ~40–45 hours (~C$5–6K).
- Takeaway: Lowest-cost stack, compliance work remains internal.
D-Link (Nuclias Connect)
- Licensing: Free on-prem software; optional hardware hub.
- Compliance artifacts: ISO alignment, structured firmware advisories. No SOC 2/FIPS.
- Labour: Compliance documentation must be produced internally.
- ~40–45 hours (~C$5–6K).
- Takeaway: Similar to TP-Link; low-cost hardware, compliance overhead is yours.
Ubiquiti (UniFi / UISP)
- Licensing: Free when self-hosted; UISP Cloud is paid.
- Compliance artifacts: Publishes CVEs and firmware notes, but no SOC 2, ISO, or FIPS.
- Labour: Slightly higher because advisories are less formalized; patch registers require more manual tracking.
- ~45–50 hours (~C$6–7K).
- Takeaway: Cheapest upfront, but heaviest compliance burden if auditors expect structured packs.
Key Takeaways
The real cost differentiator: Licensing fees versus internal compliance labour. Aruba and Cambium X carry higher license costs but save ~15–20 staff hours over 5 years by supplying audit-ready artifacts. FS.com, TP-Link, D-Link, and Ubiquiti are cheaper to license but require you to build your own compliance pack — about a week of staff time spread across 5 years.
Why unified hardware matters: Standardizing on a single switch family lowers compliance costs regardless of vendor. Once your SIEM proof, patch register, and RBAC documentation are built for one model, they scale across hundreds of devices with minimal extra work.
A critical warning: Always target compliance to the groups or divisions that actually require it. Applying full enterprise compliance frameworks to every department — including those not handling sensitive data — can balloon costs unnecessarily without improving security outcomes
Cost Scaling Example: All-Compliant vs Targeted Compliance
Assume a 100-switch division. Hardware costs vary by vendor, but here we’ll just look at compliance/licensing cost over 5 years:
All-Compliant (100% Aruba COP)
~C$250–450 per switch per year → C$125K–225K over 5 years per division.
At 10 divisions (1,000 switches): C$1.25M–2.25M.
At 20 divisions (2,000 switches): C$2.5M–4.5M.
Targeted Compliance (20% Aruba COP, 80% SMB stack e.g., Omada/FS/D-Link/Ubiquiti)
20% Aruba = 20 switches × ~C$250–450 per year = C$25K–45K over 5 years per division.
80% SMB = near-zero license cost (Omada/D-Link/Ubiquiti) or C$29.90/yr per switch (FS.com).
Total per division: C$25K–45K (vs C$125K–225K).
At 10 divisions: C$250K–450K (vs C$1.25M–2.25M).
At 20 divisions: C$500K–900K (vs C$2.5M–4.5M).
The spread is 3–5× in cost.
The only difference is whether compliance is targeted to where it’s required or applied universally.
A modular pattern that actually scales
Most institutions do not need the same bar everywhere: central IT sets the controller pattern and specifies SIEM reporting and aggregation, while divisions implement hardware tiers and may run local SIEM feeds into the central platform, retaining local monitoring responsibilities under central oversight.
Here is a simple 100-switch divisional snapshot, all 48-port PoE for easy comparison:
- Aruba CX 6100 at about C$4,160 each is roughly C$416K in hardware for 100 units
- TP-Link TL-SG3452P around C$611 to C$715 lands near C$61K to C$72K
- D-Link DGS-1210-52MP around C$870 to C$920 lands near C$87K to C$92K
- Ubiquiti USW-48-PoE at about C$799 is about C$79.9K
- Cambium EX2052-P at about C$2,015 is about C$201K
- FS S3410-48 non-PoE at about C$1,724 is about C$172K, with PoE pricing by quote
Management costs on top:
- Aruba Central On-Prem, plan roughly C$250 to C$450 per switch per year until quoted
- Omada, UniFi, Nuclias Connect, cnMaestro Essentials are zero license on-prem
- FS controller is C$299 per switch for five years, about C$29.90 per year
Audit work is the same shape in every case. You still configure and document RADIUS or SSO or PAM, point logs to the SIEM with schemas and retention, maintain a patch register, and enforce baseline configs with change control. SolarWinds NCM helps make this repeatable across brands.
Scaling out: all-Aruba versus hybrid
All-Aruba scales linearly on the licensing side:
- 5 divisions or 500 switches is roughly C$310K in controller licensing over five years plus hardware
- 10 divisions or 1,000 switches is roughly C$620K plus hardware
- 20 divisions or 2,000 switches is roughly C$1.24M plus hardware
- 100 divisions or 10,000 switches is roughly C$6.2M plus hardware
A hybrid keeps Aruba where your organization or your client insists on vendor paperwork, and uses Omada, Nuclias, UniFi, or FS elsewhere.
Assume 20 percent Aruba and 80 percent non-enterprise:
- 500 switches, with 100 Aruba and 400 non-enterprise Aruba controller share around C$62K over five years. Non-enterprise is zero if it is Omada, Nuclias, or UniFi. If it is FS, it is 400 × C$299, which is about C$119.6K over five years.
- 1,000 switches, with 200 Aruba and 800 non-enterprise Aruba controller share around C$124K. Non-enterprise is zero for Omada, Nuclias, or UniFi, or 800 × C$299, which is about C$239.2K for FS.
Compared to about C$620K for all-Aruba licensing at 1,000 switches, the hybrid trims roughly 55 percent if you mix in Omada or Nuclias or UniFi, and roughly 17 to 35 percent if you mix in FS, while still keeping sovereignty and central monitoring and only using the “compliance stack” where it is truly demanded.
Hardware Availability: The Overlooked Factor
It’s easy to focus only on licenses, compliance checklists, and feature matrices. But one of the most tangible constraints in Canada is simply getting your hands on the hardware at the right time and in the right quantities.
Aruba (HPE)
- Typically sourced through large VARs and resellers (Insight, CDW, Softchoice).
- Lead times for core models like the CX 6100/6200 series are often 4–8 weeks for volume orders.
- Spot availability exists for single units, but consistent bulk supply requires forecasting.
Cambium (cnMatrix)
- Sold mainly through wireless distributors and VARs, not retail.
- Lead times for EX20xx/EX30xx series are usually 3–6 weeks, sometimes longer if you need uniform large orders.
- Advance planning is essential if you intend to standardize at scale.
FS.com
- Ships direct from FS warehouses in the U.S. or Hong Kong.
- Small orders (1–5 units) are typically 2–3 weeks into Canada; larger shipments may take longer and can bring customs/brokerage considerations.
- Good option for pilots, but you should buffer spares if you plan a production rollout.
TP-Link (Omada JetStream)
- Widely available from Canadian retailers and online resellers (PC-Canada, Best Buy Business, Newegg).
- Lead times are usually same-day to a few days for common models like the TL-SG34xx series.
- Larger runs (100+ switches) may require coordinating with distribution, but retail channels make it easy to source incrementally.
D-Link (Nuclias Connect, DGS-1210 series)
- Similar to TP-Link, with strong Canadian retail availability (PC-Canada, Canada Computers, Best Buy).
- Delivery is typically immediate or within a week for 10–20 units; bulk purchases may need channel coordination.
- Attractive for divisional IT teams that need quick wins without VAR contracts.
Ubiquiti (UniFi/UISP)
- Broad distribution via Ubiquiti’s own Canada store, plus Amazon, PC-Canada, and other online retailers.
- Most switches are in-stock for immediate shipment, with occasional shortages during product refresh cycles.
- Very strong for fast rollouts, though not always predictable at 200–500 unit scale without forward ordering.
In practice:
- Enterprise gear (Aruba, Cambium) comes with stronger TAC and enterprise features but requires more procurement lead time.
- Retail gear (TP-Link, D-Link, Ubiquiti) is quick to source in small to medium quantities, making it easier for pilots and divisional rollouts.
- FS.com sits in between: easy enough to get single units, but longer timelines and customs considerations for scale.
Availability directly impacts resilience. If you can’t replace a failed switch in days, not weeks, downtime stretches. Many Canadian institutions hedge this risk by mixing vendors not only for cost but also for supply continuity, and by stocking spares locally.
So is there value for money
In a nutshell: If a particular contract or industry compliance demands named attestations, the enterprise stack buys you time and makes audits a touch easier by about 10 work hours a year. It does not automatically make the network more secure.
If what you really need is sovereignty and solid engineering, a hybrid gets you the same security outcomes for a lot less money.
What actually drives cost is a mix of licenses and evidence work:
- Aruba Central On-Prem is about C$250 to C$450 per switch per year. You also get vendor SOC, ISO, FIPS, PSIRT, and lifecycle documents. That usually saves around 15 to 20 staff hours over five years.
- Cambium with cnMaestro X narrows that gap with more reporting and support.
- TP-Link, D-Link, Ubiquiti, and FS keep license costs near zero or very low. The tradeoff is you build the audit pack yourself. Plan on roughly 40 to 50 staff hours over five years, slightly higher with Ubiquiti.
It is crucial to remember to targeting compliance where it is actually required.
When this is done the savings show up. Putting Aruba (or similar) in the 20 percent of places that need the regular paperwork and using lower-cost sovereign stacks everywhere else cuts compliance and licensing spend by roughly 3 to 5 times over five years at divisional scale. Hardware prices widen the spread. Aruba CX is several multiples of TP-Link, D-Link, or Ubiquiti for similar port counts. Cambium and FS sit in the middle. Availability also has value. Retail-sourced gear is easier to get quickly, which helps if you stock spares.
Security outcomes come from architecture, segmentation, timely patching, and clean telemetry. Audit outcomes come from clear evidence. Spend comes down to how much of that evidence you buy versus how much you build. For Canadian sovereignty, self-hosted controllers plus a Canadian SIEM meet the bar across Aruba, Cambium, TP-Link, D-Link, Ubiquiti, and FS. The practical plan is simple: use the enterprise stack where contracts demand vendor paperwork, use the lower-cost sovereign options everywhere else, standardize your evidence kit, and plan for lead times and spares.
Useful Sources
HPE Aruba
• Aruba CX 6100 Series overview: https://www.hpe.com/ca/en/networking/aruba-cx-6100.html • HPE Buy Canada — JL675A product page: https://buy.hpe.com/ca/fr/networking/switches/fixed-port-l3-managed-ethernet-switches/networking-cx-switch-series/hpe-aruba-networking-cx-6100-48g-class4-poe-4sfp-370w-switch/p/jl675a • Aruba Central On-Premises landing page: https://arubanetworking.hpe.com/us/en/landing/central-on-premises.html • Aruba Central Licensing Guide (PDF): https://arubanetworking.hpe.com/asset/2017932/pdf/EN/central-licensing-guide.pdf • Aruba Central On-Prem Admin Docs: https://arubanetworking.hpe.com/techdocs/central/2.5.7/content/nms/onprem/central_onprem.htm
FS.com
• Insight Canada — FS S3410-48TS: https://ca.insight.com/en_CA/buy/product/FS-S3410-48TS HPE Store • PicOS / AmpCon Licensing FAQ (PDF): https://resource.fs.com/mall/resource/picos-faq.pdf
TP-Link Omada
• Omada Software Controller (free on-prem): https://www.tp-link.com/ca/business-networking/omada-sdn-controller/ HPE Aruba Networking • TL-SG3452P product page: https://www.tp-link.com/ca/business-networking/omada-switch-l3-l2-managed/tl-sg3452p/v1/ TP-Link • Best Buy Business Canada — TL-SG3452P: https://www.bestbuy.ca/en-ca/product/tp-link-jetstream-48-port-poe-compliant-gigabit-managed-switch-with-sfp-tl-sg3452p/16576799 HPE Store
D-Link Nuclias Connect
• Nuclias Connect overview: https://www.dlink.com/en/for-business/nuclias/nuclias-connect D-Link • Nuclias Connect Solution Guide (PDF): https://www.dlink.com/us/en/–/media/resource-centre/brochures-and-product-guides/nuclias-connect-solution-guide.pdf D-Link • PC-Canada — DGS-1210-28P: https://www.pc-canada.com/item/d-link-28-port-poe-gigabit-smart-switch-including-4-combo-sfp-ports/dgs-1210-28p PC Canada • PC-Canada — DGS-1210-52MP: https://www.pc-canada.com/item/d-link-dgs-1210-52mp-ethernet-switch/dgs-1210-52mp PC Canada • Canada Computers — DGS-1210-52MP: https://www.canadacomputers.com/product_info.php?cPath=27_1046&item_id=192925 • Canada Computers — DGS-1210-28P: https://www.canadacomputers.com/product_info.php?cPath=27_1046&item_id=194873
Ubiquiti UniFi / UISP
• Self-Hosting a UniFi Network Server: https://help.ui.com/hc/en-us/articles/360012282453-Self-Hosting-a-UniFi-Network-Server Ubiquiti Help Center • UISP Cloud Hosting FAQ (Cloud vs self-host details): https://help.uisp.com/hc/en-us/articles/29600863336599-UISP-UISP-Cloud-Hosting-FAQ Ubiquiti Help Center • Ubiquiti Store Canada — USW-48-PoE: https://ca.store.ui.com/ca/en/products/usw-48-poe Ubiquiti Store • Ubiquiti Store Canada — USW-24-PoE: https://ca.store.ui.com/ca/en/products/usw-24-poe Ubiquiti Store
Cambium Networks
• cnMaestro Essentials (on-prem capable): https://www.cambiumnetworks.com/products/software/cnmaestro-essentials/ HPE Aruba Networking • cnMaestro X (paid tier): [https://www.cambiumnetworks.com/products/software/cnmaestro-x/](https://www.cambiumnetworks.com/products/software/cnmaestro-x/?utm_source=chatgpt.com • cnMatrix EX2052-P product page: https://www.cambiumnetworks.com/products/switching/cnmatrix-switch-ex2052-p/ • EX2000 Series Switches — Datasheet (PDF): https://www.cambiumnetworks.com/resource/cnmatrix-ex2000-series-switches-data-sheet/ • PC-Canada — EX2052-P: https://www.pc-canada.com/item/EX2052-P
Add-ons
• PacketFence NAC: https://www.packetfence.org • SolarWinds NCM: https://www.solarwinds.com/network-configuration-manager • CDW Canada – SolarWinds NCM Renewal Pricing: https://www.cdw.ca/search/software/?lfr=1&w=F&key=SolarWinds+NCM+Renewal+Pricing
*Compliance and Standards and critiques
• NIST CMVP (FIPS validations): https://csrc.nist.gov/projects/cryptographic-module-validation-program • NIST SP 800-140E (Implementation Guidance for FIPS 140): https://csrc.nist.gov/publications/detail/sp/800-140e/final • Schneier on Security — “The Futility of FIPS 140-2”: https://www.schneier.com/blog/archives/2005/05/the_futility_of.html • IEEE S&P critique — “The Failure of FIPS 140-2”: https://ieeexplore.ieee.org/document/9276818 • AICPA SOC 2 overview: https://us.aicpa.org/interestareas/frc/assuranceadvisoryservices/service-organization-soc-reports • “SOC 2 is not Security” (explainer): https://www.securit360.com/blog/soc-2-is-not-security/ • Harvard Business Review — “Why Compliance Programs Fail”: https://hbr.org/2018/10/why-compliance-programs-fail D-Link • PCI SSC — Official FAQs: https://www.pcisecuritystandards.org/faqs • SANS Whitepaper — “Security vs. Compliance: How to Avoid the Trap”: https://www.sans.org/white-papers/398/
Reviews & peer feedback on the management stacks (independent and community)
• Aruba Central — Gartner Peer Insights product hub: https://www.gartner.com/reviews/market/enterprise-wired-wireless-lan-access-infrastructure/vendor/hewlett-packard-enterprise/product/aruba—central Gartner • Aruba management — G2: https://www.g2.com/products/hpe-aruba-networking-management/reviews G2 • Ubiquiti management — G2: https://www.g2.com/products/ubiquiti-network-management-system/reviews G2 • Cambium cnMaestro — active user forum (release notes and operator feedback): https://community.cambiumnetworks.com/c/products/cnmaestro/37 Cambium Community
Notes
Public, third-party review coverage for TP-Link Omada, D-Link Nuclias Connect, and FS AmpCon is limited compared to Aruba and Ubiquiti. For these, vendor forums, release notes, and admin guides tend to be the most consistent sources of real-world operator feedback.
Addendum:
Sovereign Network Management Platform Comparison
This document informs on sovereign-ready network management platforms, focusing on on-premises deployment, NAC integration, MSP support, security, and pricing.
Platforms Compared
- Cambium Networks (cnMaestro)
- FS.com (AmpCon)
- Aruba (Central, AirWave)
- D-Link (Nuclias Connect, Nuclias Cloud)
- TP-Link Yes (Omada Controller) Limited (some MSP features) RADIUS; integrates w/ PacketFence Full air-gap supported**: Same as above; platform works indefinitely without cloud communication.
Legend: * Fully localizable: Can be self-hosted, but may require manual steps to disable cloud features. * Full sovereign support: Designed for sovereign infrastructure with full on-prem control, local NAC, logging, and updates. * Not suitable for sovereignty: Requires persistent cloud connectivity for management or licensing. * Free (controller): Management software has no license fee; hardware or advanced features may still cost. * Moderate / High cost: Estimated based on licensing, support, NAC integration, and hardware.
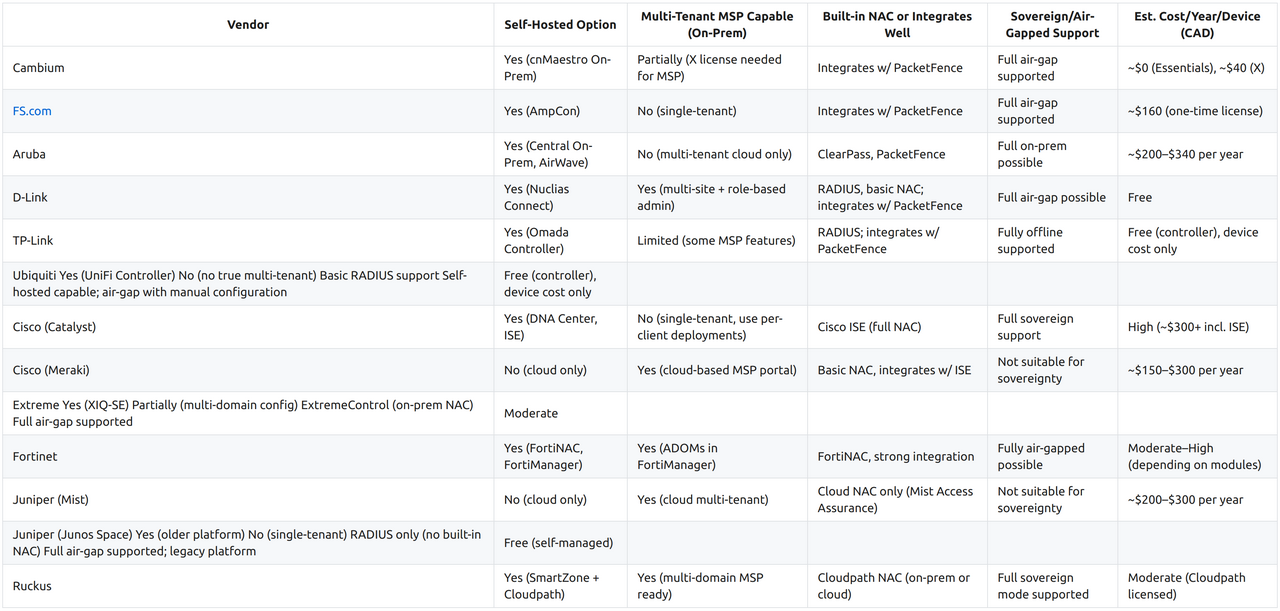
Key Insights
Budget-Friendly On-Prem Options
- D-Link Nuclias Connect – Free controller, MSP-capable, PacketFence-ready; best for small-scale deployments.
- TP-Link Omada Controller – Free local controller, basic NAC integrations, cost-efficient for SMBs.
- Ubiquiti UniFi – Self-hostable, good for RADIUS-based control, best for simplified low-cost setups.
Mid-Enterprise Sovereign Options
- **Cambium: Not SMB. Cambium delivers enterprise-light switching with better PoE, throughput, and controller tools than low-end brands. Built for sovereign deployments without cloud ties — ideal for mid-scale networks that need real performance without full enterprise pricing.
- FS.com PicOS + AmpCon-Campus – Enterprise-class switches with high PoE budget, 25G/40G uplinks, and modern NAC/SIEM integrations. Subscription-based, but fully on-prem and SDN/open-friendly.
Enterprise-Class Sovereign Solutions
- Cisco Catalyst + DNA Center + ISE – Comprehensive stack with advanced L3, segmentation, and full NAC.
- Aruba Central On-Prem + ClearPass – Full policy and identity integration with proven enterprise reliability.
- Fortinet (FortiManager + FortiNAC) – Seamless integration between security and switching; strong for zero-trust deployments.
- Extreme XIQ-SE + ExtremeControl – High-performance hardware, full on-prem NAC, and scalable architecture.
Strong NAC Capabilities
- Aruba (ClearPass) – One of the most robust identity/NAC solutions available.
- Cisco (ISE) – Deep integration across switching, wireless, and endpoint control.
- Fortinet (FortiNAC) – Tight coupling with security stack, policy enforcement.
- Ruckus (Cloudpath) – On-prem or hybrid NAC suited for education/government.
- Extreme (ExtremeControl) – Integrated NAC with strong policy tools and visibility.
Platforms Not Suitable for Sovereignty Requirements
- Cisco Meraki – Cloud-only; cannot be used offline or air-gapped.
- Juniper Mist – Cloud-native; dependent on Mist cloud for operation.
Notes on NAC Integration
- PacketFence Integration Feasible: Cambium, FS.com, Aruba, D-Link, TP-Link, Ubiquiti, Extreme, Ruckus.
- Cloud-Only NAC Options: Juniper Mist, Meraki Cloud Auth (limited).
- No Built-In NAC (Basic RADIUS Only): Ubiquiti, TP-Link, FS.com.
Licensing Trends
- Free Management: TP-Link, D-Link (Connect), Cambium Essentials, Ubiquiti.
- Subscription-Based Licensing: Aruba Central, Cisco Meraki, Mist, Fortinet (NAC & Manager), FS.com PicOS.
- One-Time Licenses: AirWave (legacy), SmartZone (Ruckus).
Hardware Capability and Performance Comparison (Switching Platforms)
When evaluating switches for sovereign-capable deployments, performance, stacking, PoE, and throughput all matter—especially for 24- and 48-port access switches. Here’s a vendor-by-vendor comparison:
Aruba (HPE Aruba Networking)
- Model Example: CX 6300 24-port PoE+, 4x25G uplinks
- Switching Capacity: Up to 880 Gbps (typical config: ~448 Gbps)
- Forwarding Rate: ~660 Mpps
- Stacking: Front-plane up to 8 units, ~200 Gbps stack backplane
- PoE: Supports PoE+, PoE++ (30W/60W/90W)
- Notes: Strong L2/L3 support, dynamic segmentation, and solid performance for enterprise campus.
Cambium Networks
- Model Example: EX2028-P (24 Gigabit PoE+, 4x10G SFP+)
- Switching Capacity: 128 Gbps
- Forwarding Rate: 120 Mpps
- Larger Model: EX2052 (48-port): ~176 Gbps
- PoE Budget: ~370W for 24-port, ~740W for 48-port
- Notes: Reliable for L2, supports basic L3 (static routes, RIP), great value in sovereign use.
Cisco (Catalyst 9200/9300)
- Model Example: Catalyst 9200 24-port PoE+, 4x10G
- Switching Capacity: 128–256 Gbps
- Forwarding Rate: ~95–134 Mpps
- PoE: UPoE+ up to 90W
- Stacking: StackWise 320/480 (320–480 Gbps stack fabric)
- Notes: Deep L3 support, high availability, preferred in complex environments.
Extreme Networks (5420 Series)
- Model Example: 5420M-24T (24-port, 4x25G uplinks)
- Switching Capacity: 328 Gbps
- Forwarding Rate: ~244 Mpps
- PoE: Up to 90W per port
- Stacking: 2x 60G stacking links
- Notes: High performance and uplink flexibility. Great for dense access or distribution.
Fortinet (FortiSwitch 124F / 148F)
- Model Example: 148F (48-port GbE, 4x10G)
- Switching Capacity: ~176 Gbps
- Forwarding Rate: ~260 Mpps
- PoE: Supports full 30W across all ports
- Notes: Good standalone switch, better when paired with FortiGate.
Juniper (EX Series)
- Model Example: EX3400-24P / EX4400-24X
- Switching Capacity: 128–456 Gbps
- Forwarding Rate: ~95–400+ Mpps depending on model
- Stacking: Virtual Chassis, ~40 Gbps
- Notes: Strong hardware; EX4400+ can handle enterprise L3 features and 25G uplinks.
Ruckus (ICX Series)
- Model Example: ICX 7150-24P / 48P
- Switching Capacity: 132–180 Gbps
- Forwarding Rate: ~134 Mpps
- Stacking: Up to 12 units, 320–480 Gbps
- PoE: PoE+ capable, standard 30W delivery
- Notes: Campus-ready, long-distance stacking is ideal for education/public sector.
Ubiquiti (UniFi Switch Pro/Enterprise)
- Model Example: USW-Pro-24-PoE (24-port PoE+), 2x10G SFP+
- Switching Capacity: ~128 Gbps
- PoE: 400W total PoE budget
- Stacking: No traditional stacking; managed under UniFi Controller
- Notes: Affordable, good for SMB and managed service environments. L2+, limited L3 (static routes).
TP-Link (JetStream via Omada Controller)
- Model Example: TL-SG3428XMP (24-port, 4x10G SFP+)
- Switching Capacity: 128 Gbps, ~95 Mpps
- PoE Budget: ~384W
- Stacking: Not supported traditionally; controller-managed for unified config
- Notes: Cost-effective, solid L2+, basic ACLs, VLANs, and 802.1X. Great in budget-conscious sovereign setups.
D-Link (Nuclias/DGS Series)
- Model Example: DGS-1210-28MP (24-port PoE+, 4x10G SFP+)
- Switching Capacity: ~104–128 Gbps
- PoE: ~370W budget
- Stacking: None; centralized management via Nuclias Connect or on-device
- Notes: Best for SMBs and low-cost deployments. Supports 802.1X, basic NAC when combined with external tools.
FS.com (PicOS/CloudController + PoE Switches)
- Model Example: S5860-48XMG-U (48-Port Multi-Gig PoE++, 4x25G SFP28 + 2x40G QSFP+ uplinks)
- Switching Capacity: ~640 Gbps
- Forwarding Rate: Not listed
- Stacking: Not designed for stacking; high-performance standalone
- PoE: Up to 740W, supports PoE++ (90W)
- Notes: High-end hardware for open SDN environments. Managed via AmpCon-Campus, which requires a subscription license:
- 1-Year License per Device: C$176.00
- 3-Year License per Device: C$244.00
- 5-Year License per Device: C$299.00 Each switch requires a license. Includes support, updates, and remote automation. AmpCon-Campus replaces the previously free AmpCon.
Performance Summary
All reviewed switches are wire-speed and capable of line-rate forwarding. Differences emerge in stacking throughput, PoE power budget, and uplink flexibility.
- Aruba: Enterprise-grade performance with dynamic segmentation and high-capacity stacking – good for flush budgets
- Cambium: Enterprise-light switching with strong L2 and basic L3 features; better hardware and management tools than SMB-class vendors, ideal for mid-scale sovereign deployments
- Cisco: High-end fabric, deep L3, and stacking scalability; good for complex deployments if cost is not an issue
- Extreme: Strong stacking bandwidth and PoE; reputation as a top-tier option for high-performance access
- Fortinet: Likely good for integrated firewall/NAC deployments; reputed solid standalone performance
- Juniper: Hardware capable of advanced features and multi-gig uplinks; If used without MIST cloud
- Ruckus: Maybe for campus or education networks; long-distance stacking and mid-range pricing
- Ubiquiti: Budget-friendly, controller-managed switches for basic L2+ sovereign needs
- TP-Link: Low-cost L2+ switch with Omada integration; practical for small sovereign networks pending not being blacklisted by the US
- D-Link: Free controller, decent PoE; solid NAC integration with PacketFence for SMB
FS.com: High-performance open-platform option with powerful PoE and no cloud lock-in
Cisco/Extreme lead in fabric and stacking bandwidth
Aruba/Juniper offer performance with advanced segmentation
Ruckus/TP-Link/Ubiquiti may provide strong value at lower TCO
Cambium: Enterprise “lite” with seemingly strong highly functional software (and deployment tools – and available enterprise grade support structure.
- Policy-Based Automation (PBA) cnMatrix switches support PBA, enabling zero-touch provisioning. Devices are profiled automatically, assigned to appropriate network segments, and configuration is removed when they disconnect. This reduces manual errors and operational effort.Cambium Networks+1
- Zero-Touch Deployment via cnMaestro The combination of cnMatrix switches and cnMaestro (cloud or on-prem) allows full lifecycle management—deployment, monitoring, segmentation—without per-port manual setup.Cambium Networks+1
- Cambium Networks Installer (formerly cnArcher) A mobile app (iOS/Android) for wireless device configuration—subscriber modules, radios (PMP, ePMP, cnWave 5 G, 60 GHz). Supports alignment tools, performance testing, firmware updates, and onboarding to cnMaestro. Targets wireless setup automation.Cambium Networks
- cnMaestro’s Assists Engine A proactive health-scoring system. It scans Cambium devices (switches, APs, routers, fixed wireless nodes), calculates an “Assists Score” indicating config or security issues, and highlights problem devices at system, site, and device levels.Cambium Networks+1
- Comprehensive Design and Analytics Tools
- LINKPlanner for fixed wireless “what-if” modeling (terrain, distance, antennas).Cambium Networks
- cnHeat with 1-meter GIS integration for precise wireless heatmap pre-planning.Cambium Networks
- Wi-Fi Designer for floor-plan based AP placement and coverage simulation.Cambium Networks